
A CIO’s job – to deliver highly available, interconnected systems and acceptable end user performance – was hard enough back in the days when all apps and systems ran under the same roof. Not to mention, back then we knew where end users were – in the office. If we wanted to access our email on the road, IT issued us locked-down devices that required us to go through clunky and slow virtual private network (VPN) connections. For a CIO today, looking back must seem like the good old days, where most resources were under direct control and expectations were not set by consumer market capabilities, like always being on-line, interchangeable devices, videoconference capability in my pocket or backpack.
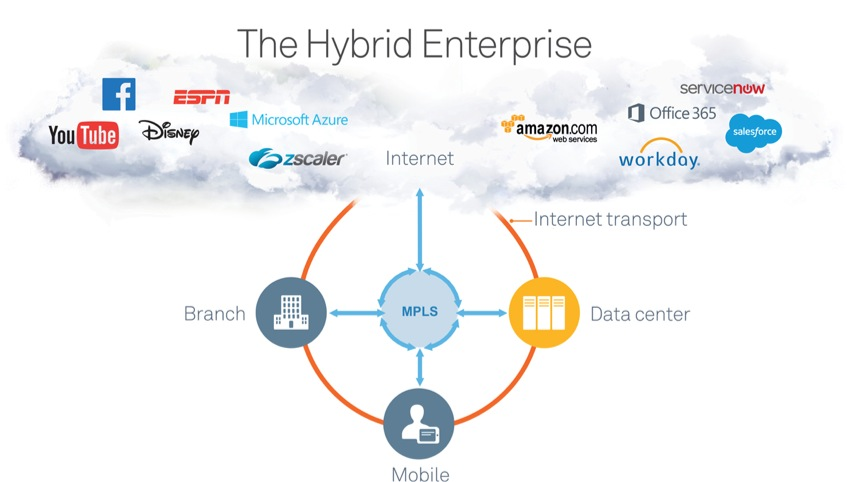
Companies today operate with one foot on-premises and one in the cloud. This combination of private and public assets delivering essential business services is known as the “hybrid enterprise,” and it has become the new normal. While this model can reduce costs and improve employee productivity, it can also be a nightmare for IT to manage. It is not enough to provision cloud apps and move on. CIOs need visibility, optimization and control across hybrid clouds and networks to ensure that all on-premises, cloud, and SaaS applications perform. After all, consider the furor that would sweep through your organization if email goes down or you cannot access important files stored in the cloud.
The one decision a CIO cannot afford to make is to try to keep everything “in house.” That would put the company at a severe competitive disadvantage; 75 percent of enterprises expect to have hybrid cloud deployments by the end of this year, and that number is only going to climb higher, according to Gartner. As the cloud grows, on-premises computing continues as well, and will continue for the foreseeable future.
To quote James Staten, former Forrester analyst and now chief strategist of the Cloud+Enterprise Division at Microsoft:
“We know that cloud services and cloud platforms are here to stay and should be considered part of your overall IT portfolio but how much of that portfolio will these services occupy in your future? For most companies – and probably all enterprises – your future won’t be 100 percent cloud. And your business units and line employees have already ensured that it won’t be 0 percent cloud. So what’s the right number?”
The hybrid enterprise model makes perfect sense and also poses a number of critical decisions to make when planning your IT systems landscape. Do I have a SaaS alternative option or do I need to continue to run a commercial software package? Should I build a private cloud or share a public cloud? Or both? What do I host internally – where and why? What’s the best way to provide access to all applications for our workforce – whether they are at major sites, small branches, or mobile warriors? Do you provide access via more expensive, but highly reliable and predictable MPLS links – a.k.a. a private network – or build secure paths across the Internet? Deploying applications in the cloud via SaaS options and providing access via inexpensive public networks can shorten time to provisioning, and on the surface, promise less IT workload to manage.
Yet, the hybrid enterprise comes with hidden costs. Having dozens of cloud and SaaS providers leads to dozens of different, and often incompatible, architectural roadmaps up and down the entire technology stack – an IT management nightmare. So when a business process or workflow moves across the hybrid landscape, is it really fair to expect the IT teams to quickly troubleshoot and solve problems within such a diverse architecture, much of which falls outside their purview where responsibility lays with a service provider or SaaS vendor? Try telling that to your CEO. . . .
The key to success in our new reality is what we in the IT business call “end-to-end visibility.” It sounds like an empty buzz term, but it refers to a critical capability IT must have today: leveraging a single management console to see all activities in real-time all the way from the remote end-user’s device, through any network they may use, to the app running in the datacenter or the cloud.
For example, consider a network administrator with a multinational company who has implemented a centralized management console in order to monitor all apps, users and sites holistically across the entire global network. A real-time alert appears that indicates SharePoint has an issue, so he drills down to view all apps, and confirms all are nominal except SharePoint. He examines each site running SharePoint, and sees all are fine except for one remote office. The current path selection policy directs SharePoint traffic over MPLS, and the console shows the MPLS pipe is almost at capacity. So he modifies the path selection policy for collaboration technologies like SharePoint to route over public Internet when MPLS is not available. Problem quickly identified and solved.
Achieving this level of end-to-end visibility requires five key building blocks:
Network and application-aware path selection capability: Directs traffic on the appropriate network. A typical branch configuration has three paths, one based on MPLS, a second based on an Internet link combined with a secured overlay connecting the branch back to the data center using Internet protocol security (IPSec), and a third path exiting directly to the Internet.
Dynamic tunneling capability with a central control plane: Provides for secure backhauling of branch traffic to the corporate data center across the Internet using IPSec.
Simple interface to zScaler (or other cloud-based security service providers): As companies embrace local Internet breakouts, they must also strengthen their security environments within the branches themselves. To do so, enterprises typically implement secure Web gateways (SWGs) that analyze specific ports like HTTP/HTTPS ports and often use SWGs in combination with advanced threat detection (ATD) to detect the more advanced attacks. Now these capabilities are being made available as a cloud service. Interfacing with a security service provider like zScaler enables local Internet breakouts without requiring further investment in on-premises Internet security appliances.
Inbound QoS: For managing local Internet breakouts and protect business Internet traffic against surges in recreational Internet traffic. For example, the finite bandwidth of the local Internet pipe can be filled as branch users consume a variety of business-critical SaaS applications combined with less critical and bandwidth-heavy applications like YouTube. Implementing a QoS capability that manages traffic from the destination instead of from the source like with traditional QoS effectively slows down less critical inbound traffic to make room for more business-critical flows, thus protecting experience and productivity for users of those applications.
Unified management plane: one management app that provides administrators with an intuitive interface and management plane based on high-level abstractions such as applications, sites, uplinks, or networks that match the way they see their IT environment.
Improving Visibility Affects The Bottom Line
Consider the case of NKT Cables, a global supplier of cables and cable solutions to the energy sector, which was expanding and rapidly outgrowing its IT infrastructure.
Headquartered in Cologne with subsidiaries across Europe and Asia/Pacific, over 3,500 employees, and revenues of around €1.2 billion (about $1.6 billion at current exchange rates). The company has approximately a dozen datacenters and server rooms across Europe, China, and Australia. Each site had its own physical and virtual servers, plus local storage, services and backup, and that made managing the large estate increasingly challenging. To make the situation more complex, localized backups made it difficult to provide comprehensive data protection, which had negative implications for disaster recovery.
NKT Cables decided to migrate to a branch-converged infrastructure to simplify its infrastructure, centralize resources and manage IT more efficiently. As a result, the company now has a centralized backup solution, making data more secure and consolidating its disaster recovery solution to one place. This level of standardized deployment at site level reduces the time IT must spend managing systems and applications, and provides end-to-end real-time visibility to enable much faster identification and remediation of issues as soon as they arise.
Now, I know you may be thinking: “Yeah, but so much of what goes wrong is outside my company’s control, even our CIO’s – what good does it do to pinpoint another vendor’s problem?” Consider that the sooner a problem is found, or even anticipated before it hits, the sooner somebody can address it – even if it is not your IT team.
That point does lead into the struggle to achieve control now that IT typically only has control of just a fraction of our hybrid environment. Here are some approaches I have found work well in this very common scenario.
All hands on deck: You cannot fight these battles alone. Pull in your critical service providers and your trusted peer network to help shed light on what is happening ‘out there’. This means reaching out to other IT executives and banding together to address issues like compromised server farms.
Follow the traffic: Find out where the bottlenecks and blockages are in the network. That will help you pinpoint where the problem is coming from. It’s essentially an issues heat map.
Be predictive: Look for trends in your data. Did this problem come on quickly or slowly? Is there a trend that is leading toward an even bigger disaster six hours from now? Be predictive in your thinking to avoid getting stuck in reaction mode.
Achieve the necessary levels of control, and the math becomes as simple as 1+1=2. Visibility+Optimization=Control. This may seem simplistic, but this equation refers to IT’s ability to keep systems running at optimum levels and ensure information is available to all employees in headquarters, remote offices, or on the road.
Visibility not just of a particular device, network or app, but end-to-end visibility that lets it detect and fix problems before the end user even notices. Optimization not of discreet infrastructure but optimizing how your business runs. And control not just at layer 4, but all the way up to the application layer. These are our new norms for ensuring IT meeting business objectives.
Rich Hillebrecht is vice president and CIO at Riverbed Technology, a provider of WAN optimization tools that are used by over 26,000 enterprises worldwide.





Be the first to comment