
A lot of compute is moving to the edge, and that means that networking and storage has to follow it. In many cases, that means bringing advanced functionality for all three – albeit in smaller capacities – out to the edge. But in other cases, it doesn’t make either technical or economic sense to do this.
That is precisely why Broadcom has tweaked its “Trident 4” StrataXGS BMC56880 series of ASICs for enterprise-class datacenter switches to have security features that protect the edge of the network from the safety and centrality of the core. This requires the core to be beefed up so it can do a lot more packet processing and monitoring of myriad edge devices.
Broadcom has come to this conclusion as edge computing has gotten more intense and it has provided enterprise-class switches for the edge, Fred Olsson, director of product marketing for the Trident product line, tells The Next Platform. Three years ago, Broadcom had connection monitoring and other security features added to edge switch ASICs.
“For the first time, we are able to see all the flows and detect all of the traffic going through the edge,” Olsson explains. “But there were two drawbacks. First, it is very expensive to upgrade the edge network because there are thousands and thousands of devices. Corporate networks typically have many generations of equipment out there and they use them for a long time, and when companies acquire other companies, they end up with different mixes of switches. But there is only one core, and it is a much smaller number of devices. But more importantly, this approach to edge switching and monitoring is not very good at detecting distributed events because each device is only seeing a tiny portion of the network. Once you are in the core, you can see everything. So the right place to do this, we have learned, is in the core.”
That said, having security at the edge of the network and at the edge of servers inside of DPUs is also a good idea, and Olsson readily admits this. You need to secure all of these different layers, and we think every DPU needs firewalls and intrusion detection and prevention systems because you really can’t trust anything on the many layers of the network these days.
For its part, Broadcom is scaling up the packet processing and monitoring capabilities in the Trident 4 line with the new Trident 4-X11C, which is shortened to the Trident 4C. And the security approach that this Trident-4C device will allow will significantly beef up the security of the entire corporate network.
In the past, Olsson explains, enterprises focused at the firewall and the links to the wide area network, and there is still a little bit of that going on. And with many devices from the outside of the network linking in – PCs, laptops, cell phones, all kinds of IoT devices, and so on – protecting at the firewall was no longer sufficient. And so network probes were added to switches, which opened up some packets and did some analysis to try to figure out if anything nefarious was going on.
The trouble with this approach is that the switch ASICs did not have enough oomph to inspect all of the packets that traversed them. The typical probe was done on one in a thousand or more packets. That low sampling rate was necessary because bandwidth builds as you move from the edge to the aggregation layer to the core of the network. If you have 1 Gb/sec or 10 Gb/sec links at the edge, you have terabits per second running inside of the network and you have to analyze billions of packets per second. You can’t probe all of that.
Until now, that is, with the Trident 4C.
To use an analogy, every passenger boarding an aircraft has a background check and goes through the metal detector instead of 1 in 1,000. And, importantly, once you do that, you can observe connection-level patterns across the network. So sticking with the airport analogy, if you analyze all connections and all passengers, you might notice that there are ten passengers going from New York City to San Francisco that fit a high-risk profile and then you can surmise that something is possibly amiss.
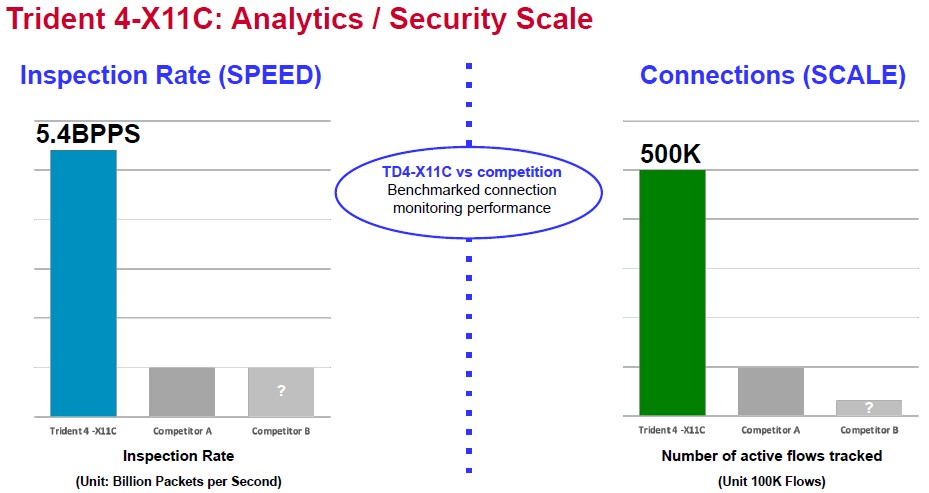
With such an approach, the switch needs to have a ridiculously high packet inspection rate, and that is what makes the Trident 4C different from the regular Trident 4 chip, which was launched and started sampling in June 2019 with a 25.6 Tb/sec device that could drive 64 ports at 400 Gb/sec and then expanded in December 2020 with denser 25.6 Gb/sec and 12.8 Tb/sec devices using PAM4 SerDes. All of these Trident 4 switch ASICs are monolithic designs and they are etched by Taiwan Semiconductor Manufacturing Co using 7 nanometer processes. The Trident 4C device takes that 12.8 Tb/sec version of the improved Trident 4 line and jacks up the packet inspection rate to a whopping 5.4 billion packets per second and a similarly whopping 500,000 simultaneous connections that can be monitored.
Here is how Broadcom thinks the Trident 4C stacks up against the competition in enterprise core networking:
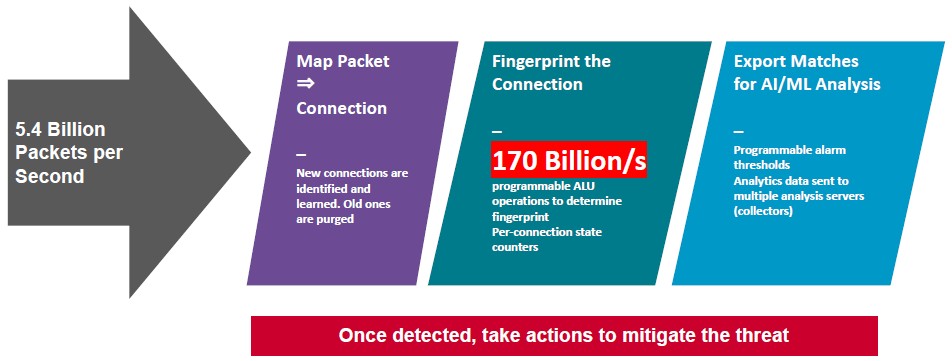
Being able to juggle that many packets and connections is one thing, but it doesn’t get you anywhere unless you can do fingerprint the packets and do some mapping between packets to look for anomalies. And that is why the new bit of circuitry added to the Trident 4C – what Broadcom calls an “ultra-high performance analysis engine” – is so important.
This analysis engine can process 170 billion operations per second and fingerprint collections of packets and flows. And while the Trident 4C does not have integrated machine learning capabilities to do intrusion detection and prevention, it outputs the suspicious telemetry as well as the benign telemetry that allows existing network analyzers that do have AI capabilities to learn from the data it parses from the network.
This analysis and fingerprinting engine knows when a flow is new and when it is aging out, and it knows what packets are part of what flows, and so it can see what kinds of flows are coming from what servers. And it is supported by much higher MAC learning rates for network flow topologies than the normal Trident 4 ASICs, which can handle about 25,000 stations per second. The Trident 4C has a MAC learning rate of 125,000 stations per second, which matches the high packet processing and fingerprinting rates of the design.
So customers using the Trident 4C will, for instance, be able to see the pattern of port scans that a typical virus does when it has infected one server and is looking to spread to other servers. Similarly, distributed denial of service (DDoS) attacks (including fragmentation attacks that crush servers as packets are intentionally shredded and fed to their network ports), other kinds of weakness probing, and unauthorized data transfers all become visible from the core.
If you tried to do this from the edge, you would have to time synch telemetry coming off thousands of devices and build a giant fingerprinting engine using software running on a server. It is better, and faster, to do all of this in the silicon at the core as Broadcom has done.
Don’t be surprised when hyperscalers and cloud builders demand such features in the “Tomahawk” line of switch ASICs. Or that they simply ask for 25.6 Tb/sec and 51.2 Tb/sec Trident 5C ASICs for their core switches. For all we know, they are already in the plan.
Broadcom expects for switch designers to use the Trident 4C in fixed-port 1U switches with 32 ports running at 400 Gb/sec, compact modular switches with eight modules and driving a total of 128 ports running at 100 Gb/sec as well as a chassis switch with eight line cards driving the same ports and speeds. For advanced chassis designs, Broadcom sees a modular switch with a pair of Trident 4C ASICs with one driving eight line cards, each with 48 ports running at 25 Gb/sec, and the other Trident 4C as a hot spare to improve network reliability. This is what it calls a “single switch chassis.”





Be the first to comment