For the Linux Foundation, this summer in part has been spent pulling in new projects aimed at building an open architecture around the quickly emerging world of agentic AI, the latest rage in the ever-expanding generative AI universe.
In June, Google donated its Agent2Agent (A2A) protocol to The Linux Foundation, a standard for AI agents communicating and collaborating that brought with it the support of such heavyweights as Amazon Web Services, Cisco Systems, Microsoft, Salesforce, SAP, and ServiceNow. A month later, Cisco donated AGTNCY, a protocol developed by the vendor’s Outshift incubation arm that is designed to help organizations find and manage the best agents for the job they need done.
As we noted, Cisco executives say AGNTCY creates an “internet of agents” that can be run on any framework or vendor, run multi-agent systems securely security and at scale, and monitor their performance.
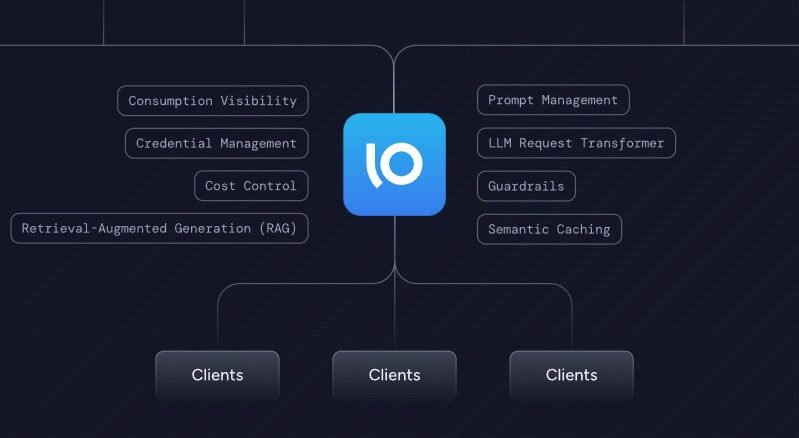
Now comes the Agentgateway project, with Solo.io, a startup best known for its cloud-native networking applications and that last year introduced its commercial-grade Gloo AI Gateway as an open source data plane aimed at enhancing AI agent-to-agent and agent-to tool communication. This gateway has a focus on key functionalities like security, observability, and governance.
At the recent Open Source Summit Europe in Amsterdam, The Linux Foundation announced that Solo.io was donating Agentgateway. Foundation executive director Jim Zemlin described the Agentgateway project as a secure management layer for interactions between AI agents that have to communicate across myriad environments and development frameworks and need to support the accelerating number of protocols.
Support For A2A And MCP
Agentgateway comes to The Linux Foundation already supporting A2A and the Model Context Protocol (MCP) developed by Anthropic, the company behind the Claude LLM, as a standard for allow agents to connect with external systems and share data from a broad range of sources. Contributors include AWS, Cisco, Huawei, IBM, Microsoft, and Red Hat.
“In a nutshell, Agent Gateway is serving as the gateway in between your agents, in between your agent and the MCP server, in between your agent and your large language model, to help mediate that traffic to apply security policies such as authentication, authorization, to be able to do governance and control and also provide observability on top of that,” Lin Sun, vice president of Solo.io, told The Next Platform.
The company was founded in 2017 by Idit Levine, its chief executive officer, whose background includes work with Dell Technologies, Intigua, CloudSwitch (acquired by Verizon in 2011), and DynamicOps.
For AI Agents, A Necessary New Gateway
Solo.io is no stranger to gateways and proxies, developing its own Gloo Gateway, a Kubernetes-native API gateway built atop the open source Envoy proxy for cloud-native applications and microservices architectures and handles such tasks as traffic management, security, and observability. A year ago, the company introduced the Gloo AI Gateway that makes it easier and faster for developers to integrate AI capabilities into cloud-native applications.
In March, Solo.io unveiled kagent, an open agentic AI framework for Kubernetes that was designed to help users build and run AI agents to accelerate Kubernetes workflows. A month later, at KubeCon + CloudNativeCon Europe 2025 in London, Solo.io announced it was contributing kagent to the Cloud Native Computing Foundation (CNCF).
When thinking about the need for a dedicated AI agent, Solo.io executives knew they could use Envoy, given their experience with it, Sun said. That experience included efforts by Solo.io developers to use it to create a lightweight proxy to handle mutual TLS for services in a service mesh. After a year of writing code based on Envoy, they were able to do it, but what they had was a configuration so complex, only three people on the team could really understand it, she said.
It wasn’t scalable and they ditched the effort, choosing instead to rewrite the proxy component for Istio’s Ambient Mesh, using Rust. That experience influenced the development of Agent Gateway. It wasn’t practical to think that existing API gateways could be used for agentic AI, with the speed, scale, and adaptability it needs.
Moving Past Envoy
“When we started the Agentgateway project, we knew what Envoy can do and we knew the pain point with Envoy and we didn’t think it was worth our time to invest to … re-architect Envoy to support leading A2A or MCP protocols,” Sun said. “We decided to start from ground up using Rust, leveraging some of our expertise, even some of all our code in Istio, and reuse them in Agentgateway to build this gateway specifically for AI.”
Agentgateway was built as a unified data plane for connecting AI agents and includes the ability to integrate existing REST APIs as agent-native tools. It includes a built-in developer portal tool providers and agent developers can use for managing agent-based connectivity, can integrate with such agent frameworks as LangGraph, Agents SDK, Claude Desktop, and kagent, and run on bare metal, virtual machines, containers, and Kubernetes.
The Agentgateway project boasts about its support for the A2A and MCP protocols. However, it’s taking a wait-and-see approach with AGNTCY, Sun said.
“I don’t see a lot of momentum behind that project, to be very honest with you, because I serve on the CNCF Technical Oversight Committee, so I’ve been looking at a lot projects,” she said. “One of the key criteria is, what is the community behind it? How many folks, how many GitHub stars?”
Sun also noted that AGNTCY doesn’t support A2A, having instead its own has its own communication protocol called Agent Connect Protocol (ACP), which allows agents to communicate even if built through disparate tools or platforms. That also shouldn’t be confused with IBM’s ACP (Agent Communication Protocol).
“It is three agent-to-agent protocols, and I just feel like the momentum behind the A2A is strong by looking at the community,” she said. “That’s what we are endorsing for Agentgateway. I’m not saying we can’t endorse any other protocol, but we would like to see the momentum before we actually pick up any other protocol.”
Taking a step back, Sun said a gateway is important for agentic AI, but it’s only a part of what’s needed. She envisions a mesh for AI agents.
“We want people to be able to focus on agents and the MCP server and not worry about security authentication and all that and policy control, because I do believe there is a notion of a mesh that can take care of this,” she said. “My ultimate goal is a gateway shouldn’t play inside of the cluster. I think gateways traditionally play a very good role to control traffic going out of the inside of the cluster. I almost want the gateway to be more transparent to the user.”
Users building agents or MCP tools shouldn’t have to worry about the core business logic of their agents and tools.
“Whoever operates them can apply policies and gain visibilities through a mesh that’s for AI,” Sun said. “I do think Agentgateway can play a key role in that mesh. We’re not entirely there yet because we’re building the building block, which is very, very important at this moment. I just think with Agentgateway being donated to The Linux Foundation, we open up the project for more collaboration, more momentum.”


Be the first to comment