Physical electronic systems routinely leak information about the internal process of computing. In practical terms, this means attackers can exploit various side-channel techniques to gather data and extract secret cryptographic keys. To be sure, side-channel attacks conducted against electronic gear are relatively simple and inexpensive to execute. Such attacks include Simple Power Analysis (SPA) and Differential Power Analysis (DPA). These noninvasive techniques analyze power consumption while a device is performing routine operations with secret keys and algorithms.
Differential Power Analysis
Differential Power Analysis is a form of side-channel attack that monitors variations in the electrical power consumption or electro-magnetic emissions of a target device. The basic method involves partitioning a set of traces into subsets, then subsequently computing the difference of the averages of these subsets. Given enough traces, extremely minute correlations can be isolated—no matter how much noise is present in the measurements.
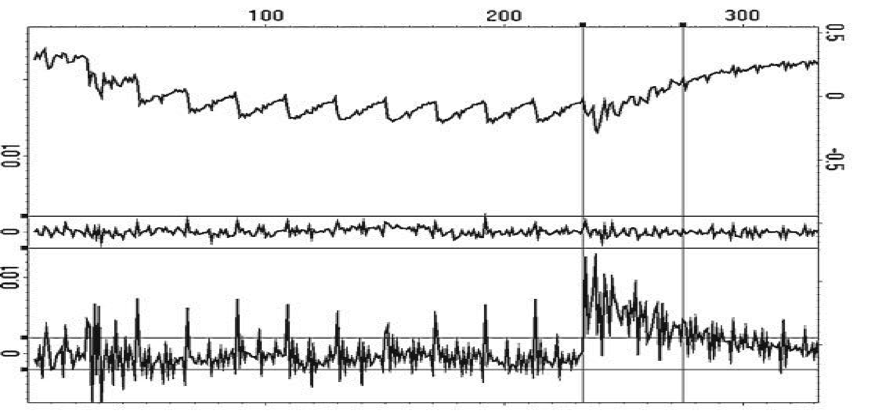
Image Credit: Rambus Security Division (via “Introduction to Differential Power Analysis”)
A typical DPA attack comprises 6 primary stages: communicating with a target device; recording power traces while the target device performs cryptographic operations; signal processing to remove errors and reduce noise; prediction and selection function generation to prepare and define for analysis; as well as computing the averages of input trace subsets and evaluating DPA test results to determine the most probable key guesses. Additional DPA variants include reverse engineering unknown S-boxes and algorithms, correlation power analysis (CPA), probability distribution analysis, high-order DPA and template attacks.
Specific DPA countermeasure techniques include decreasing the signal-to-noise ratio of the power side channel by reducing leakage (signal) or increasing noise, for example, by making the amount of power consumed less contingent upon data values and/or operation (balancing); introducing amplitude and temporal noise; incorporating randomness with blinding and masking by randomly altering the representation of secret parameters and implementing protocol-level countermeasures by continually refreshing and updating cryptographic protocols used by a device.
Simple Power Analysis
Simple power analysis is a collection of methods for inspecting power traces to understand a device’s operation, including identifying data-dependent power variations during cryptographic operation. SPA is primarily focused on exploring features that are directly visible in a single power trace or made clear by comparing pairs of power traces.
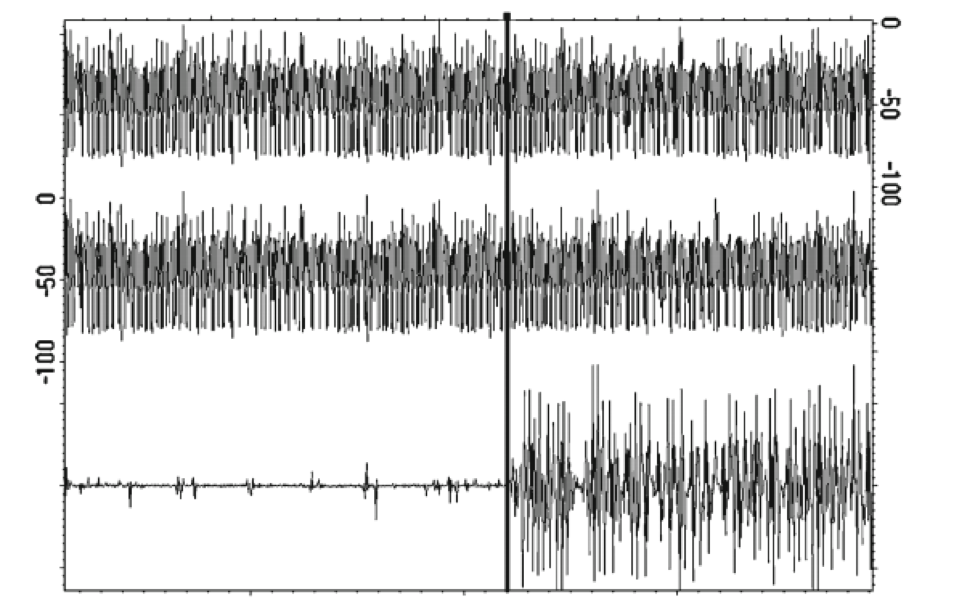
Image Credit: Rambus Security Division (via “Introduction to Differential Power Analysis”)
Essentially, SPA exploits major variations in a power consumption, although this technique is typically incapable of extracting keys from noisy measurements. Nevertheless, SPA offers attackers an extremely effective and efficient method of obtaining the data necessary to determine secret keys. Indeed, implementations of modular exponentiation for public-key cryptography algorithms such as RSA [Rivest-Shamir-Adleman] and Diffie-Hellman may use a key-dependent sequence of square and multiply operations, while scalar multiplication in Elliptic Curve Cryptography [ECC] may be implemented using a key-dependent sequence of double and add operations. Both could potentially leak the value of the key from a single operation.
Eliminating significant leaks is a major first step to preventing SPA vulnerabilities. As such, system designers should employ constant execution paths and eschew taking conditional branches on secret data. When possible, processing primitives and instructions should be selected from those known to leak a reduced amount information in their power consumption.
Evaluating side-channel vulnerability
In addition to offering a full suite of DPA countermeasures, Rambus has designed a DPA Workstation (DPAWS) that evaluates resistance to a variety of side-channel attacks (SPA, DPA, HO-DPA and EMA) across a wide number of devices and platforms including smartphones, tablets, PoS terminals, CPUs, TVs, set-top boxes, FPGAs, smart cards and NFC tech.

Image Credit: Rambus Security Division
DPAWS provides security researchers with a highly intuitive UI paired with enhanced data visualization that creates an integrated, project-centric analytic environment specifically designed to optimize the efficiency of side-channel analysis. Both flexible and scalable, DPAWS easily integrates with a wide range of industry tools such as Matlab, as well as Python and other scripting languages. The DPA Workstation also supports full cipher coverage (AES, RSA, ECC, DES and SHA), large dataset handling, as well as high-speed collection and analysis of billions of traces.
Interested in learning more about side-channel attacks? You can check out our DPA countermeasures product page here and our article archive on the subject here.
