
All things being equal, all IT organizations would like to have the highest level of security on their machines that is possible. Until they have to actually pay for that security and weave it into their systems, that is. Then they start doing the math, trying to figure out how to lock down the key machines in the datacenter. Skyport Systems, a startup that is creating what it is calling hypersecure infrastructure, or HSI for short, has also done the math and has cooked up a combination of hardware and software that will allow companies to lock down the key assets in their clusters without breaking the bank trying to put it on all of their machines.
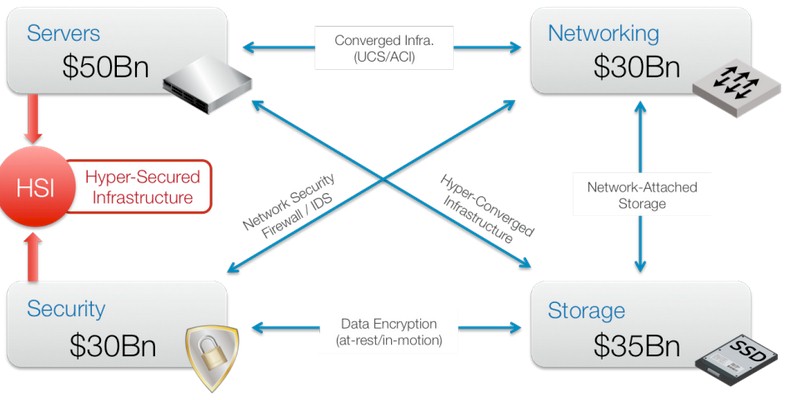
There are four key pillars that underlie the applications in the datacenter, and we are all well familiar with them – servers, networking, storage, and security. But the key observation that Skyport’s founders have made is that each time you arc two of these together and tightly couple them, you create a new kind of platform that addresses very specific needs in the market and, consequently, creates an opportunity to make some money. Mashing up servers and networking gave us modular systems (sometimes called converged infrastructure) like the Unified Computing Systems from Cisco Systems. Tightly coupling networking and storage created network-attached storage; mashing up servers and storage creates hyperconverged systems like those available from Nutanix, VMware, SimpliVity, Pivot3, Maxta, and so on.
“The initial use cases on of these scenarios was to simplify an onerous integration task for end users, with a narrow market insertion and then you drive it home,” Doug Gourlay, who is the corporate vice president in charge of sales, marketing, production management, and systems engineering at Skyport, explains to The Next Platform. (Gourlay was in charge of systems engineering at datacenter switching upstart Arista Networks and before that worked on the Catalyst and Nexus switching lines at Cisco – including the integrated switching in the UCS modular servers.) “And then you evolve it to a platform, with multiple points of integration from DevOps systems and programmatic systems. As we kept drawing all of these lines on the chart, we saw this noticeable gap here. Nobody in the last decade has effectively integrated security with the server. We have security in the operating system, and in agents and apps and all sorts of stuff. But not the server.”
In the old days, when companies wanted more secure machines, they got the ruggedized versions of Solaris or AIX Unix and put key applications on these platforms; SE Linux, short for Security Enhanced Linux, is an analog in the Linux world. But Gourlay says that these solutions are too cumbersome in that these super-secure operating systems required substantial changes to both the operating system and the applications – something that companies are loathe to do. Server virtualization solved part of this problem by abstracting away the operating system and allowing another form of containment, but does not get around the central question, which is this, as Gourlay puts it: “Why is my Xbox One more secure than my servers?”
The central issue that IT shops struggle with, says Stefan Dyckerhoff, CEO at Skyport, is that every enterprise has to open up their networks to let in consumers, customers, and partners. The security moat that wraps around the infrastructure has lots and lots of bridges over it, and the network is not really the right root of trust anymore.”
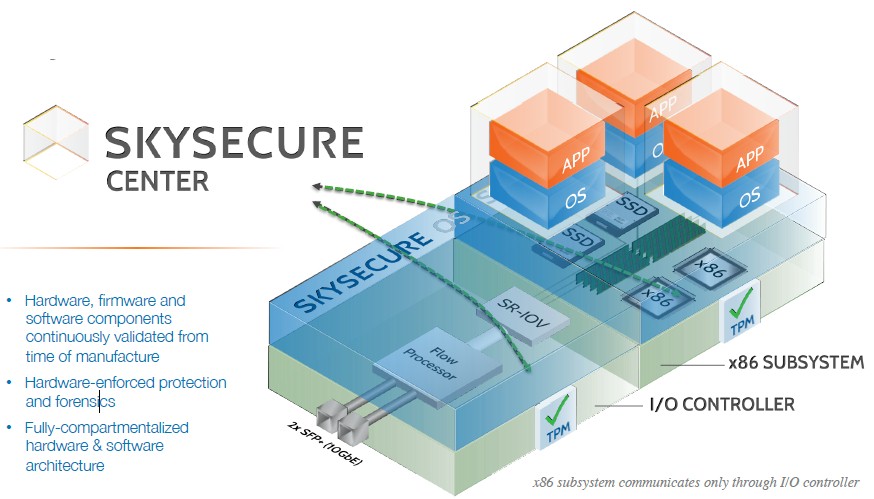
The assumptions with a hypersecure infrastructure platform is that you need to create a root of trust in the hardware of the server and that workloads running on the machine will be compromised at some point and that you have to do comprehensive and continuous monitoring to find it when it happens. If you can establish the server itself as the root of trust – rather than the network linking outsiders to systems – then to task of finding breaches and fixing them becomes easier. “We will minimize the threat surface of the machine and if it ever does become compromised, we are going to ensure that it does not become a landing pad for all sorts of other attacks inside your infrastructure,” explains Dyckerhoff. The idea is that a Skyport system is hard to break into, and even harder to break out of. The Skyport software watches packet flows, operating system activities, application transactions, and everything that is going on inside of the machine and creates audit trails for the whole shebang.
Dyckerhoff is the first to admit that companies can build HSI machines themselves today – but the integration task is a pain in the neck. The key is that you need to establish a root of trust inside of the iron, and that means embedding a trusted compute platform (or TPM chip) inside of the machine. Skyport has added SE Linux on top of that and has abstracted away some of the annoyance of using it. The security stack includes hypervisors and orchestration controls for virtual machines and microsegmentation for the networks that feed the VMs and bare metal machines. The Skyport stack includes traffic analysis, packet mirroring, application whitelisting, and other functions that would require the integration of tools from maybe eight or nine different vendors.
One of the secrets of the SkySecure integrated security stack for servers is that it has one complete and curated set of metadata for all systems software and applications. You don’t have to weave it all together to sort out if something is a threat. The SkySecure servers are physically hardened and tamper-resistant, and the SkySecure Center management console is deployed as a service, rather than a locally running piece of software, to make consumption a lot easier. You don’t need a team of PhDs from a systems integrator – which is precisely the point of mashing up servers and security.
Skyport doesn’t think that companies will deploy these machines everywhere in their clusters – although in some cases this could happen where security is of paramount importance. “In the enterprise, customers will use these systems in the places where they are most exposed and in the places where they run their critical control systems,” says Dyckerhoff. So customers use Skyport machines in the network DMZ for business-to-business transactions and also in branch offices that are outside of the datacenter and its network backbone and much hardware control. Importantly, all of the nodes that control DNS, Hadoop, vSphere, OpenStack, Active Directory, or LDAP authentication should be locked down with HSI machinery, says Dyckerhoff. Add it all up, it might represent somewhere between 1 to 3 percent of the worldwide server installed base.
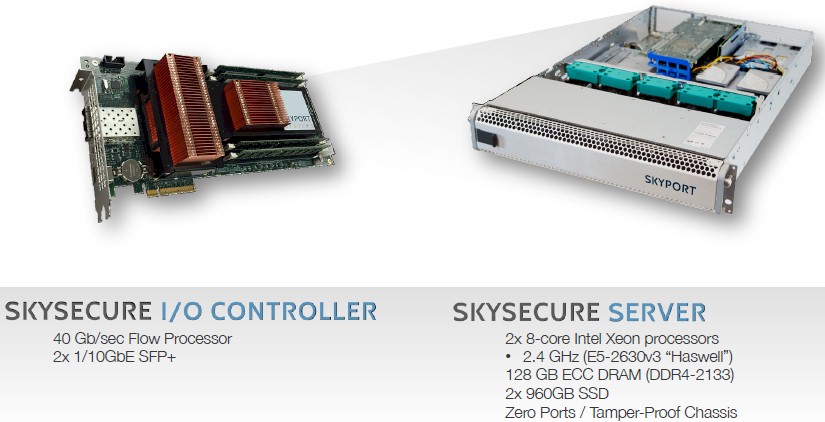
The SkySecure Server is based on components from Intel and includes two of the chip maker’s Xeon processors as well as two TPM security chips that have been used in the past to create secure desktop machines. It uses a hardened version of the Xen hypervisor coupled with SE Linux and the TXT security on the Xeon processors as well as the add-on TPM chips to lock down the system software stack. The server has an I/O module that is the only way into and out of the server, which has two 10 Gb/sec Ethernet ports and a 40 Gb/sec flow processor for network analysis that feeds into the SkySecure Center service. The chassis of the server has no ports and is tamper proof; it is not a particularly beefy machine, but in a base configuration it has enough oomph to be useful. IT distributor Avnet, which also builds Open Compute machines as well as reselling all kinds of servers, does the final manufacturing for Skyport. By choosing Intel and Avnet as its hardware partners, Skyport can get the critical “Made In America” label that will help it secure Federal and state agency contracts for its wares.
Gourlay tells The Next Platform that a hefty configuration of this server will cost on the order of $10,000 to $12,000 and that the subscription to the SkySecure Center service will cost $2,500 per server a month. Skyport is taking orders now and will be putting out the servers and monitoring service for production deployments later this summer.
“Why is my Xbox One more secure than my servers?”
With a global installed base of around 40 million servers, and assuming Skyport could get somewhere between 1 percent and 3 percent of the base using its hardware and services, that is a total addressable market of between $5 billion and $15 billion.
Skyport was founded in 2013 and has 55 employees and came out of incubation at Sutter Hill Ventures, where Dyckerhoff is still a managing director; prior to joining Sutter Hill, he spent decades doing all kinds of work at Juniper Networks and Cisco Systems, ranging from designing ASICs for switches to running marketing operations. In April, Skyport raised $30 million in its second round of funding; its Series A round was $7 million, presumably all from Sutter Hill, which incubated the company with co-founders Rob Rodgers (chief architect), Michael Beesley (CTO), and Will Eatherton (vice president of engineering). Foer the second round of funding, Sutter Hill brought in Index Ventures and Intel Capital. The three company founders all know Dyckerhoff from jobs they held at Juniper and then Cisco designing routers.


Be the first to comment