
The rapid adoption by enterprises of hybrid cloud and multicloud environments along with the rise of the Internet of Things, a much more remote workforce and other trends that have contributed to the increasingly distributed nature of modern IT has put the vast amounts of data that is being generated in a precarious position. No longer created, collected and store in central datacenters sitting behind corporate firewalls, workloads and data are now bouncing between public clouds, between clouds and on-premises datacenters, from the edge through the cloud to the datacenter and back again.
Data is everywhere and in multiple environments, putting it at greater risk from cyberthreats from increasing sophisticated criminal and nation-state operations that now have a much larger attack surface to work on. There’s no way to put a firewall around such a decentralized situation, so other means of security – including encryption – are getting more work as organizations look to shield sensitive data from cyberattacks and stay in compliance with the growing numbers of government regulations and standards – think the European Union’s General Data Protection Regulation (GDPR) or California’s Consumer Privacy Act (CCPA) – designed to protect the privacy of business user and consumers.
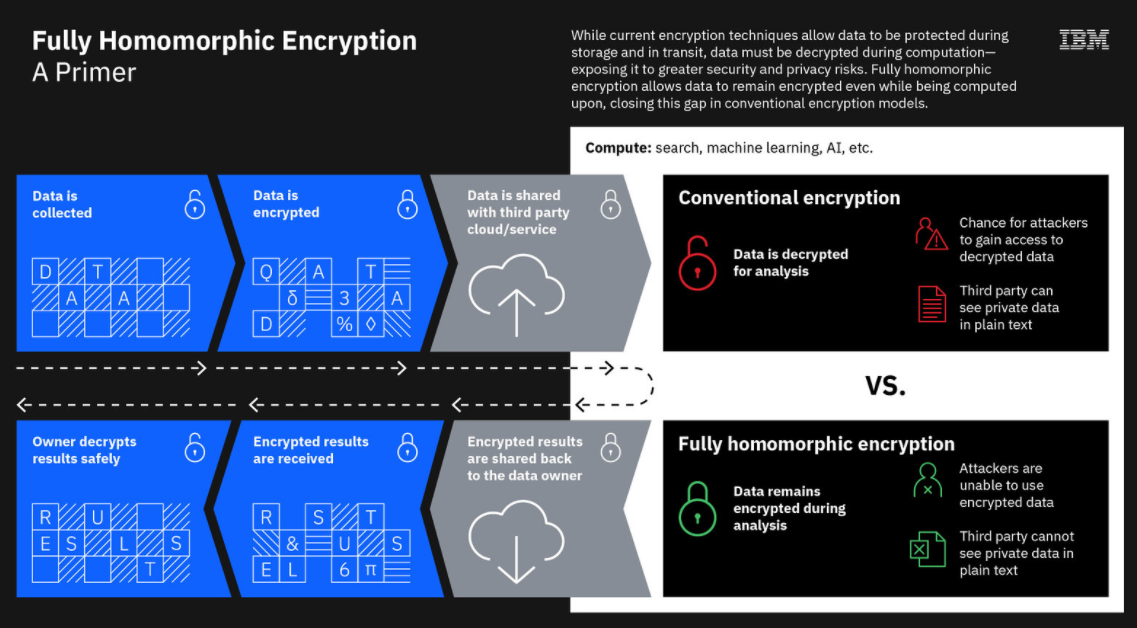
However, even modern encryption has its shortcomings. Enterprises now can encrypt data when it’s at rest and when it’s in transit. However, when they have to start putting it to work – to process and analyze it – it must be decrypted, exposing it to cyber-criminals who want to access or steal it or to third parties that may be able to see it. In a hybrid cloud world, the risk is high.
Enter Fully Homomorphic Encryption (FHE). Initially discussed in the 1970s but not demonstrated until 2009, homomorphic encryption enables data to remain encrypted even as organizations process and analyze it in the cloud or in third-party environments, protecting it from bad actors and the eyes of others who are not supposed to see it. Once the calculations or other mathematical operations are run on the encrypted data, the results will be corrected once they’re decrypted.
“It’s important because data is more portable than ever,” Eric Maass, director of strategy and emerging technology at IBM Security Services, tells The Next Platform. “We are in a very fluid state. Infrastructure is everywhere. Once upon a time, we built monolithic applications and the data, for all intents and purposes, was well contained within sight of a monolith of sorts. Today, applications are very hybrid in nature. There’s computing that’s happening on-prem. There’s aspects of that computation that may happen in a hybrid fashion on infrastructure-as-a-service provider. Data is just being sent wherever it’s needed, basically to be utilized by highly distributed applications. In a hybrid cloud era, we expect that the infrastructure has become far more distributed and therefore [so is] the computing and therefore where the data needs to flow in order to perform that computing.”
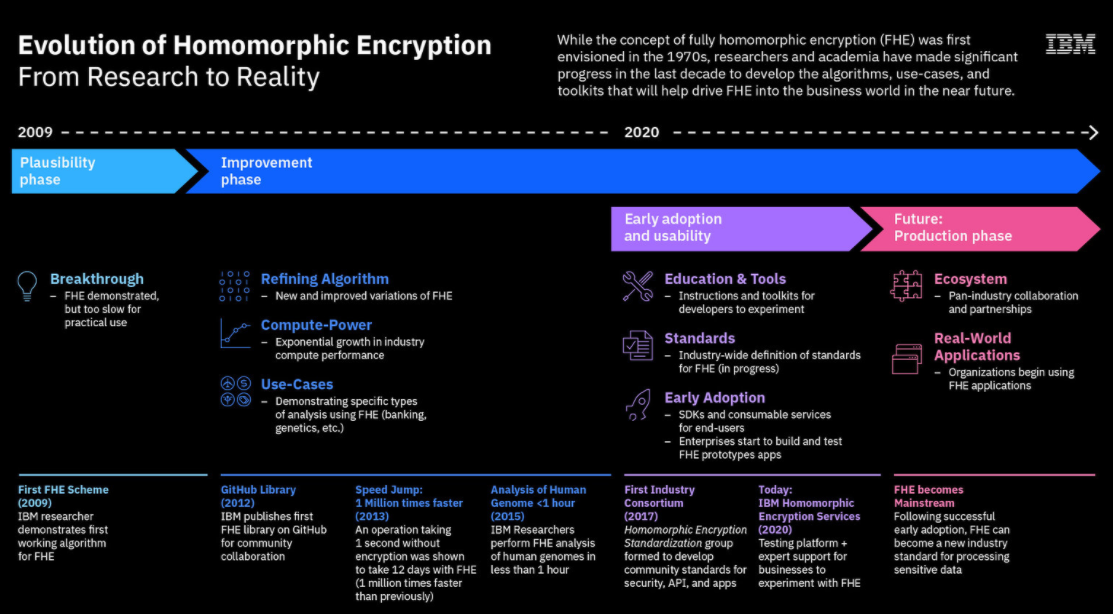
IBM has been an active player in the development of FHE, with IBM researcher Craig Gentry in 2009 demonstrating the first working algorithm for homomorphic encryption, though it was far too slow for practical use. More recently, Big Blue this summer ran successful FHE field trials and released a FHE toolkit for MacOS and iOS, Apple operating systems, adding Linux and Android later. This month, announced its IBM Security Homomorphic Encryption Services, a scalable offering hosted on IBM Cloud that gives organizations an environment for experimenting with the encryption technology and consulting and managed services to help them with their efforts.
Over the past decade, IBM and other companies have worked to make processing encrypted data faster. The demonstration in 2009 showed it could be done, but at the time it could take days or weeks to run FHE calculations that otherwise would take seconds on decrypted data. The organizations worked to improve the algorithms used for FHE and IBM created open-source libraries, such as HELib and the aforementioned FHE Toolkit. The result is homomorphic encryption that is more functionally viable and ready for wider use. The algorithms IBM is using on its new cloud service are founded on lattice-based cryptography, an encryption technology that is being developed to push back at the oncoming cyberthreats that will arrive with more widespread quantum computing.
The combination of expanded compute power and advanced algorithms, FHE can now be performed at seconds-per-bit, an important measurement that indicates that homomorphic encryption is fast enough to be used in increasing numbers of use cases and early trials. Examples of uses cases can include healthcare facilities that want to give patient data to clinical researchers to help them search for cures for a disease but can’t do so now because regulations prevent exposing such sensitive data to third parties or retailers who want to do more targeted marketing but are worried about jeopardizing trust of their consumers by using their data in a way that exposes it.
“Over the last 10 years, a lot of what it comes down to is just the math,” Maass says. “It gets down to finding efficiencies in the way that the math is being done to improve the speed. Way back in the day, a single digit being computed in an FHE-enabled application took somewhere around a half an hour. We improved that. … It’s still multiple times slower than performing the same calculation on clear text data, but it’s improved to the point where a lot of the computation that we make here about basic analysis, statistical analysis of data, that sort of stuff, could be done in a way that’s almost imperceptible.”
IBM’s FHE Services offering has two key goals: To give enterprises a cloud-based environment trying out the technology and running experiments and as a way of educating organizations and offering them services and support from IBM cryptography experts, both with the aim of preparing them to build and deploy FHE-enabled applications. The tools were developed by IBM Research and IBM Z, offering templates for common FHE use cases, including encrypted search, AI, machine learning and analytics. The IBM Cloud infrastructure can scale as needed.
There continue to be challenges to mass adoption of homomorphic encryption, Maass says. FHE is complex and requires a lot of compute power – as much as 100 times the compute resources of operations on plaintext data – the lattice encryption keys and other FHE-specific technologies are not mainstream and may need particular infrastructure, and coding for FHE may be different from traditional methods. Applications and data need to be prepared in particular ways when dealing with FHE.
“Data preparation really has a lot to do with what use case you plan to implement with the technology,” he says. “The simplest example is if you picture a spreadsheet of data, you have rows and columns. Traditional databases have rows and columns of data. Often with [FHE] data preparation, the columns need to become rows and the rows need to become columns. There are certain types of math that needs to take place in which we’re twisting and turning the data in ways that it’s not natively coming out of a traditional relational database. It’s not overly complex, but it does take understanding those constraints and use cases in order to plan for that. Clearly, systems as they exist today for storing data within these organizations are not going to be natively compatible if we need to start twisting and turning the data that way.”
Likely candidates for using FHE include organizations in highly regulated industries – healthcare, financial services, retail and the like – and those using data in highly collaborative and distributed, which is getting more common with the growing adoption of hybrid clouds.
That said, FHE will be a targeted sort of technology, not one “designed to be a wholesale replacement for all forms of encryption,” he says. “We’re going to still see basic asymmetric and symmetric encryption that exists for data at rest and data in transport continue to be the primary way to do that job. They do it well. They do efficiently. This is really targeted at data that needs to be protected as it’s being put into an untrusted domain, shared with a third party, maybe being utilized in an untrusted cloud computing environment where it’s out of our hands and we want to make sure that it’s not going to be exposed as we’re computing on it. There’s a time and place for every form of cryptography and we see this as complementary to the data at rest and data in transit algorithms and techniques that are out there today.”
It’s going to take time, but two to three years down the road homomorphic encryption will have evolved from a fresh-from-the-lab technology to one that is more widely used, Maass says. Gartner analysts earlier this year predicted that by 2025, at least 20 percent companies will have projects on the books that include FHE, up from about 1 percent now. IBM’s FHE Services offering is a step in that direction by getting organizations prepared for the technology’s evolution.





Be the first to comment